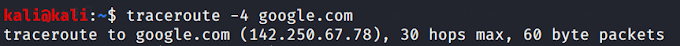
traceroute command in linux with examples
Traceroute is a command in linux which prints the route that a packet takes which includes the details about the hops in between i.e the whole route from the host machine to the target Below pictures including with the respective examples are provided for better understanding. I…
How to hack camera of an android mobile in Kali Linux 2020
How to hack camera of an android mobile in Kali Linux 2020 For video tutorial : Click Here Disclaimer : This post is only for educational purpose .Use what you learned in a right way. To hack camera of an android mobile first 1) Open the link and copy the code : Click here 2)N…
Protect your privacy on the internet 2020 #privacy
Watch this as a video Click here Every information that you directly or indirectly give on the internet like your email address, the post you like, your phone number,these all are examples of Data Points and with these little bits of information you can be tracked on the intern…
SNIFFING | INFORMATION GATHERING | ETHICAL HACKING
SNIFFING Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools. Sinffing allows you to see all sorts of traffic, both protected and unprotected. In the right conditions and with right protocols in place, an atta…
NMAP - 1 | FINGERPRINTING | INFORMATION GATHERING | ETHICAL HACKING
NMAP | PART 1 Nmap - Network Mapper Is a free open source utility for network discovery and security auditing. It is also used to find the vulnerabilities on a network by scanning through different ports. Port scanning is the Nmap's core functionality but it is also can be u…
FINGERPRINTING | INFORMATION GATHERING | ETHICAL HACKING
FINGERPRINTING OS Fingerprinting - is the term used in ethical hacking basically refers to any method used to determine what operating system is running on a remote computer. This could be- Active Fingerprinting - is accomplished by sending specially crafted packets to a targe…
FOOTPPRINTING | INFORMATION GATHERING | ETHICAL HACKING
FOOTPTINTING Footprinting is a part of reconnaissance process which is used for gathering possiable information about a target computer system or network. Footprinting can be both active and passive. Reviewing a company's website is an example for passive footprinting and a…
ETHICAL HACKING | INFORMATION GATHERING | INTRODUCTION
INFORMATION GATHERING Information Gathering and getting to know the target systems us the first step in Ethical Hacking. Reconnaissance is a set of processes and techniques of Footprinting Scanning Enumeration These are collectively used to descover and collect information abou…
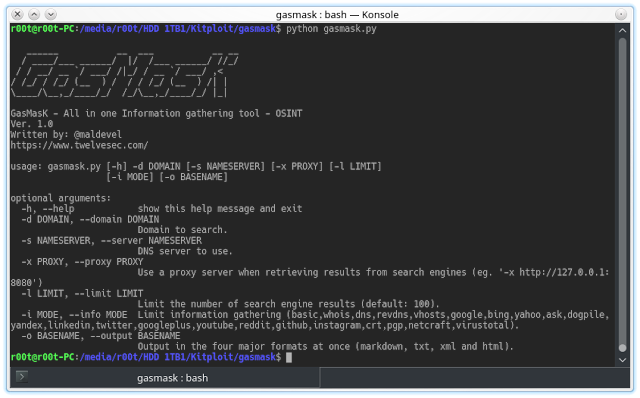
Ethical Hacking | Gas Mask OSINT Tool
Gas Mask - It is an open source intelligent tool/program which is used for information gathering. It is a very useful in penetration testing,bug hunting. It gathers information from ask bing crt censys.io dns dnsdumpster dogpile github google googleplus instagram linkedin netcra…
PROXYCHAINS | KALI LINUX | ETHICAL HACKING
PROXYCHAINS-CONFIGURATION Proxychains Proxychains is open source software for Linux systems and comes pre installed with Kali Linux, the tool redirect TCP connections through proxies like Socks, Tor, HTTP(S) and it allows us to chain proxy servers. Uses With proxychains we can h…
HOW HACKERS AVOID DETECTION | ETHICAL HACKING
HOW NOT TO BE CAUGHT BEING A HACKER Before knowing how to be anonymous on web, Let's discuss various reasons to get it's importance. It is extremely important to stay anonymous being a hacker. Let's talk about a simple example 1. We will start by assuming the attack…
Hack anyone's whatsapp,facebok, instagram and many other social media accounts
Real Hacking | How it actually Happens Watch the same as video : CLICK HERE Have you seen these messages popping up in your mail inbox or as forwarded messages in your whatsapp claiming free likes and followers for your social media accounts or get a chance to win a free iphon…
HOW HACKERS GET CAUGHT? | BANGLADESH CENTRAL BANK BREACH
HOW HACKERS GET CAUGHT? Despite what may seem like an critical task, hackers are human and make mistakes. It’s often some careless errors that will trip the criminals up and leave a trail of evidence that the police can follow. In the 2016 Bangladesh Central Bank attack, where h…
Popular Posts

zANTI Guide (Advanced Hacking Android App )(Root)

Virtual Private Networks (VPN) (Free nordVPN)
Subscribe Us
Featured Post

Mr Robot Season 1 Episode 3 Hacks Explained .
Tags
Search This Blog
Categories
ABOUT
Recent Posts
Footer Menu Widget
Copyright (c) 2020 CODE-BYTE All Right Reseved