SECRET SEARCHES FOR HACKING
GOOGLE DORKS If you are newbie, you won't belive that hackers use Google searches for most of hacks and cracks. It's called Google Dorks . We can use Google dork to find vulnurabilities, hidden information and access pages on certain websites. Check GOOGLE DORKS full in…
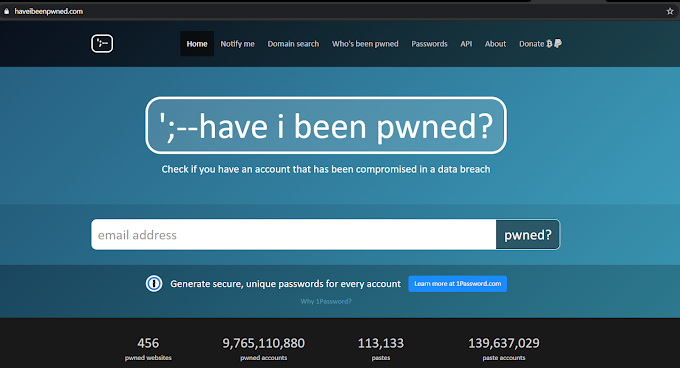
HOW TO KNOW YOUR EMAIL ADDRESS IS IN DARK WEB OR NOT?
To Know Whether our email address is in dark web or not Visit This website : click here and type your email address and click enter. If your Email Address is pwned then in this Website it shows as follows If your email address is pwned then there is high chance that your Ema…
WhatsApp resolves issue that exposed some user's phone numbers in Google search results
Recent issue in Whatsapp which leaked Whatsapp numbers in Google Search has been resolved. On June 5,2020 a researcher found that phone numbers tied to WhatsApp accounts are indexed publicly on Google Search creating what he claims is a “privacy issue” for users. WhatsApp featu…
GET ANY SOFTWARE PRODUCT KEY | WINDOWS ADOBE VMWARE PHOTOSHOP | 94fbr METHOD
Free Serial keys What is a Product Key? A product key, also known as a software key, is a specific software-based key for a computer program. It certifies that the copy of the program is original. How it works? Product keys consist of a series of numbers and/or letters. This seq…
SHELL SCRIPTING PART 4 || CUT COMMANDS IN SHELL SCRIPT
CUT COMMANDS IN LINUX SHELL SCRIPTING #2 FOR PART 1 : CLICK HERE FOR PART 2 : CLICK HERE FOR PART 3 : CLICK HERE CUT#5 Given a tab delimited file with several columns (tsv format) print the first three fields. Sample Input 1 New York, New York[10] 8,244,910 1 …
GOOGLE HACKING | GOOGLE DORKS
G oogle hacking How it is useful in Ethical Hacking feild? Hacker or Penetration tester uses Google search tricks called Google hacking tricks to gather information about the target by open web. How to hack Google, if you want to hack Google use Google Hacking Database. Google H…
SHELL SCRIPTING PART 3 || CUT COMMANDS IN SHELL SCRIPT
CUT COMMANDS IN LINUX SHELL SCRIPTING FOR PART 1 : CLICK HERE FOR PART 2 : CLICK HERE CUT #1 For each line of input, If you want to print its character on a new line for a total of lines of output. We can do this using cut command in the following way. S…
Popular Posts

zANTI Guide (Advanced Hacking Android App )(Root)

Mr Robot Season 1 Episode 3 Hacks Explained .
Subscribe Us
Featured Post

Mr Robot Season 1 Episode 3 Hacks Explained .
I Post articles related to Technology,Programming ,Hacking
Tags
Search This Blog
Categories
ABOUT
Recent Posts
Footer Menu Widget
Copyright (c) 2020 CODE-BYTE All Right Reseved